46 WordPress Support Forums and Resources to Best Assist You
When you do have a question regarding your WordPress website that you can’t find an existing answer for, make sure you have a complete description

When you do have a question regarding your WordPress website that you can’t find an existing answer for, make sure you have a complete description

WordPress plugins add functionality and features to your website, helping you customize it to your specific needs. Whether you want to optimize your website for search engines, improve security, or add an online store, there’s likely a plugin for it.

Ransomware is a rapidly evolving threat, with attackers increasingly turning to remote techniques that target network…

WordPress 6.8.2 is now available! This minor release includes fixes for 20 Core tickets and 15…

Netrality Data Centers has announced the completion of a high-density data hall at its Indianapolis Telcom…
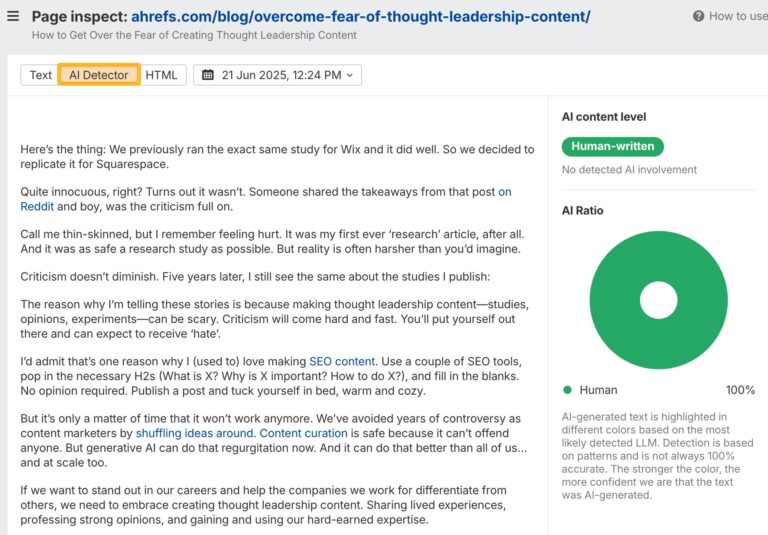
AI Overviews are AI-generated content, which means they can contain hallucinations. Google uses “grounding” to improve…

Why doesn’t your doctor’s office feel like a safe place anymore? Most people assume their medical…

Narwal Prime Day is Here! From July 8th to 11th, Grab Narwal Freo Z 10 at…

Cloud infrastructure spending in Mainland China reached US$11.6 billion in the first quarter of 2025, marking…

The WordPress Foundation is proud to launch WordPress Credits, a contribution-focused internship program that brings university…

It’s impossible for anyone to list all the best digital marketing conferences as nobody’s been to…

Publicly Disclosed Zero-Day Vulnerability in Microsoft SQL Server CVE-2025-49719 is an Important information disclosure vulnerability affecting…

If you’re trying to choose between WordPress and Laravel for your next website, you’re not the…

SUSE, a global provider of enterprise open-source solutions, has launched a new service aimed at meeting…

We’ve attended dozens of SEO conferences and found some standout events that consistently deliver value, insight,…

The MacBook Air is already an amazing laptop, but what more can you get if you…
I’ve helped WordPress users navigate a lot of different privacy laws, but Saudi Arabia’s Personal Data…

The healthcare sector continues to be a prime target for cyber adversaries, with threat actors constantly…

IREN has announced a $130 million investment to acquire 2,400 units of NVIDIA’s next-generation Blackwell B200…