September 2025 Patch Tuesday: Two Publicly Disclosed Zero-Days and Eight Critical Vulnerabilities Among 84 CVEs
Publicly Disclosed Zero-Day Vulnerability in Windows SMB CVE-2025-55234 is an Important elevation of privilege vulnerability affecting…

Publicly Disclosed Zero-Day Vulnerability in Windows SMB CVE-2025-55234 is an Important elevation of privilege vulnerability affecting…

Cisco has unveiled a new wave of artificial intelligence capabilities designed to transform the operations of…
When I first started blogging, promoting my content on social media was a major time drain….

EchoStar is preparing for one of the most significant spectrum transactions in recent years, announcing that…

Core Technology that Powers Security for AI What follows is a breakdown of the core Falcon…

An amazing 6K monitor cheaper than all the rest? Or just a cheap knockoff? I spent…

A Visionary Leader in MDR In a crowded MDR market, independent analyst evaluations like The Forrester…
I got my hands on the new Terramaster D1 SSD Plus. This little portable SSD enclosure…
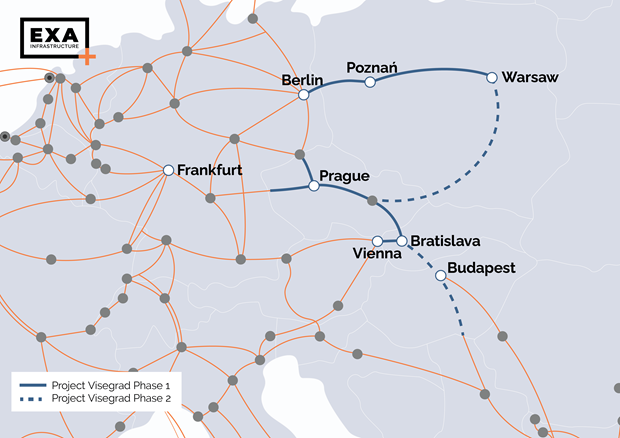
EXA Infrastructure has unveiled plans for Project Visegrád, a large-scale fiber backbone deployment set to reshape…

CrowdStrike data scientists are members of a team of cybersecurity researchers that recently released EMBER2024, an…

Article Performance Data from Ahrefs Linking websites The number of websites linking to this post. Get…

We know that AI assistants like ChatGPT access search indices, like Google and Bing, to retrieve…

Choosing a platform for your online community is a big decision. Pick the wrong one and…
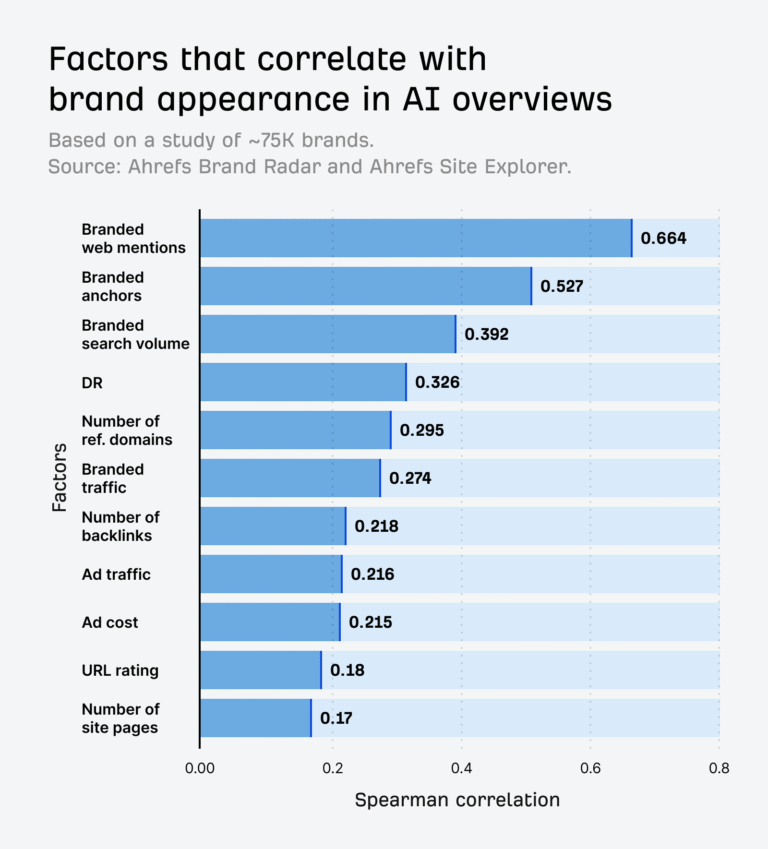
When you search on the internet, there’s a good chance LLMs are involved somewhere in the…
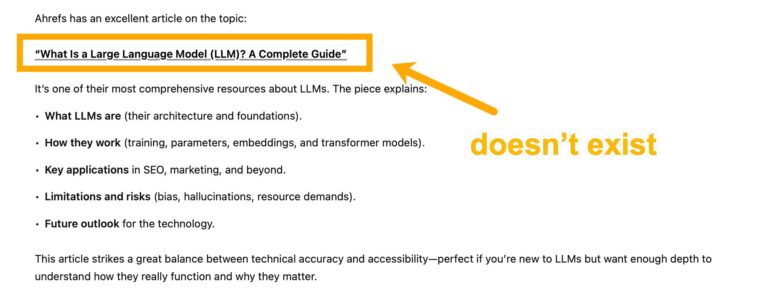
AI assistants like ChatGPT and Claude can hallucinate URLs and direct visitors to non-existent pages on…

When someone fills out a form on your website, it should be a chance to connect…

Cloudflare has unveiled an expanded suite of security capabilities for its Zero Trust platform, Cloudflare One,…

A full house of attendees gathered in Portland, Oregon, for WordCamp US 2025, with thousands more…