The BEST New Tech I Saw At CES 2026!
I spent the last 3 days walking around CES 2026 and interacting with all the new…

I spent the last 3 days walking around CES 2026 and interacting with all the new…

Types of AI Tool Poisoning Attacks Tool poisoning attacks can take many forms, each designed to…

In this video, I share the real-world services I stopped self-hosting in my home lab and…

I’m excited to announce CrowdStrike’s agreement to acquire SGNL, a leader in identity-first security. This acquisition…
If you’re collecting event registrations, payments, or course sign-ups in WordPress, it makes sense to give…
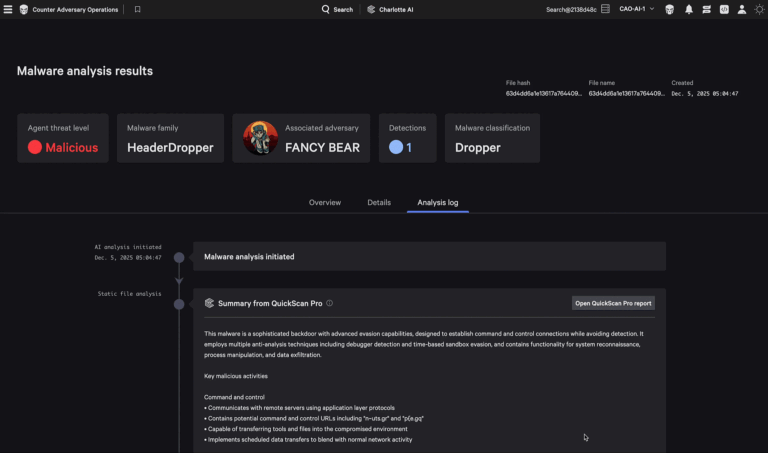
Under the Hood: How It Works The Malware Analysis Agent replaces the manual process of analyzing…
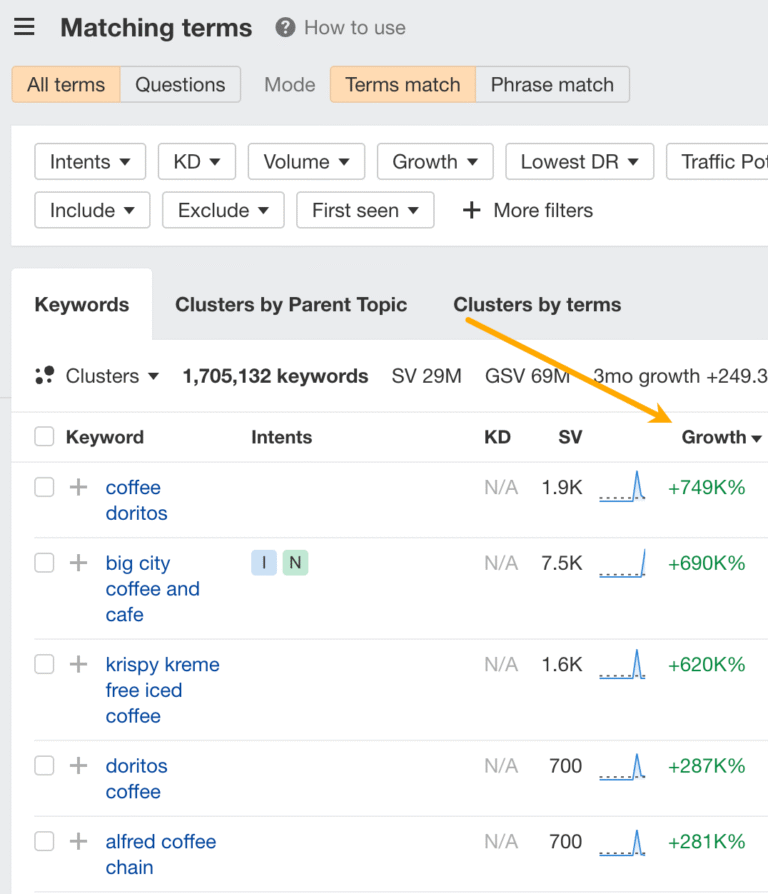
1 cast of a very jonas christmas movie 11000 >999% 2 ₹99/- deals on flipkart 450…

1 what is today 4,870,000 2 what is my ip 2,500,000 3 what to watch 2,420,000 4 how to…
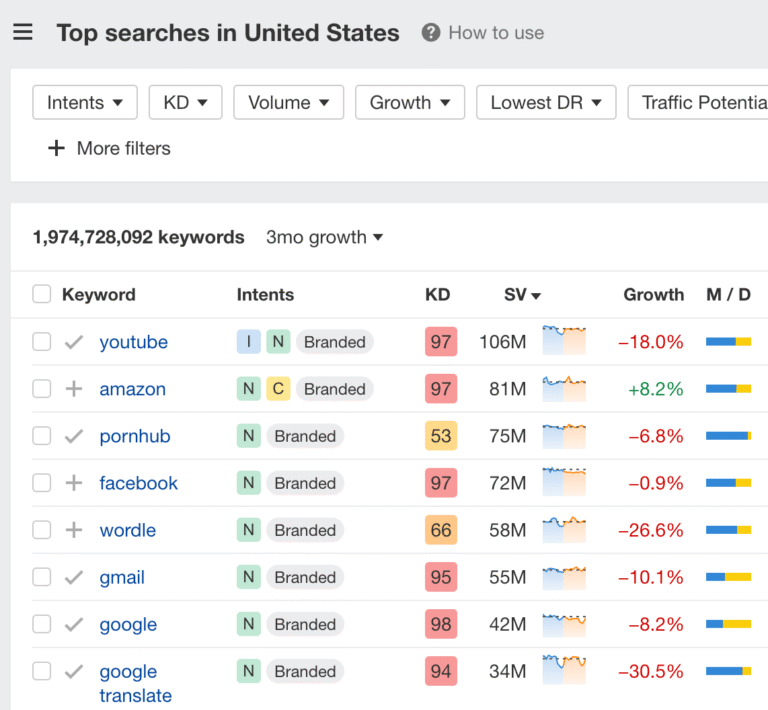
Get the week’s best marketing content As of 2026, the most searched thing on Google is…
Keeping network diagrams up to date has always been one of the most frustrating parts of…

Most WooCommerce store owners hit a wall trying to turn visitors into paying customers. Sales trickle in…

It’s a new year, and a perfect time for fresh starts, especially when it comes to…

As the year comes to an end, we’re taking a moment to look back at some…

As IT environments grow more complex and adversaries move faster, security and IT teams need a…

Every AI marketing disaster you’ve seen—the cringeworthy fake influencers, the obviously robotic copy, the brands caught…

December has been an incredible month for the WordPress community as we wrap up a landmark…

Automating processes on your WordPress website doesn’t have to be complicated. Tools like n8n are powerful,…

How does Apple’s most powerful Mac compare against the most powerful PC? Let’s find out… ⚡️Buy…