It has never been more important to prevent cyber attacks. Every company relies on the internet at some point in their business model, so it is vital to protect your technology.
We’ll explain the best simple security measures that will help you prevent cyber attacks and keep your business safe.
Why is Cybersecurity Essential?
Table of Contents
No modern business can run without cybersecurity measures. It is as essential as a business license to your company’s day-to-day operations.
To keep your business safe, invest in cybersecurity measures at every level of the company’s system. Employee phones, office computers, and company-wide servers all play a role in data protection for businesses and in keeping sensitive information safe.
The strongest strategies value openness and interoperability in cybersecurity. Cloud technology means you need good security across the entire network, including other companies’ infrastructure, not just your local devices.
Interoperable solutions allow each company to have its own cybersecurity strategy without compromising the network’s security as a whole. Otherwise, incompatible systems might conflict with each other and make the whole process less secure.
What is a Cyber Attack?
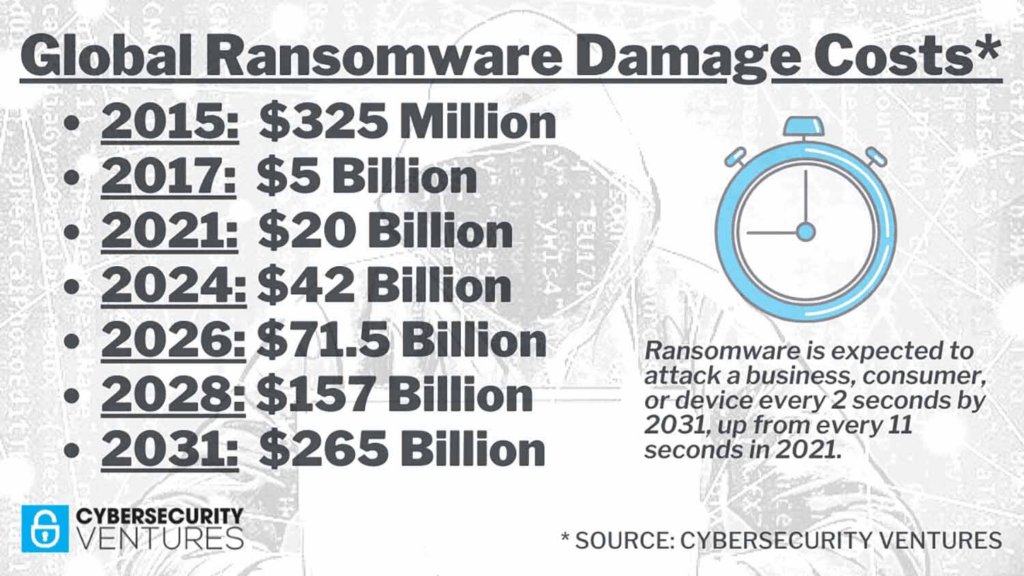
A cyber attack is any malicious attempt to damage or steal information from a business or private individual. They can cause huge amounts of damage to a company’s infrastructure and reputation. This damage can cost thousands, or even millions of dollars, to fix!
So it’s easy to see why cybersecurity measures are a priority for business owners. Before putting up defenses against cyber attacks, you first need to know what you’re facing.
Types of cyber attacks
There are several different types of cyber attacks. Understanding the differences between these attacks is the first step to preventing them.
The most common cyber threats are system intrusion attacks, social engineering (like phishing), and denial of service attacks.
System intrusion
System intrusion attacks do damage to your computer’s basic web applications through things like malware. Malware is any kind of program or file that deliberately damages a computer or compromises data.
Ransomware attacks are when cybercriminals use malware to encrypt your data, then refuse to unlock it until you pay them the money they demand.
You should carry out regular security assessments to make sure that it’s difficult (ideally impossible) for a system intrusion to happen. Identifying bugs and carrying out regression testing with Global App Testing, for example, help strengthen any weak points.
Social engineering
Many cybersecurity strategies focus on devices and their software. However, 82% of cyber attacks involve the human element — social attacks, errors, and misuse. Many of these attacks rely on real people, who have legitimate access to those devices, to find a way in.
Phishing is when a user enters their credentials into what they think is a trusted website, but it’s really a fake site set up by cybercriminals.
Employees should look out for any suspicious emails – typos, incorrect domains, and phrases like ‘URGENT’ or ‘ACT NOW’ are all common signs of a phishing email.
You can double-check when a domain was registered by looking it up on a domain registry.

Denial of Service attacks
Denial of Service (DoS) attacks overwhelm servers with a huge wave of requests, making them inaccessible to real users.
Of course, your servers might crash because of a surge in genuine web traffic, but DoS attacks are on a much larger scale and deliberately damage a network.
You can make your website less vulnerable to DoS attacks by scaling up the amount of traffic your servers can process, but this can be expensive. A cloud-based security system can reduce the impact of a DoS attack by spreading the demand across multiple servers.
Using unlimited bandwidth residential proxies can also provide online privacy, by acting as an additional boundary between your computer and the websites you visit.
Best Security Measures to Keep your Business Safe
Okay, so you know what you’re up against. We’ve explained the basic security measures to prevent each of the major types of cyber attacks, but now let’s take a more holistic view.
These strategies can be implemented at every level of your company’s system and defend against a range of threats.
Complex passwords
Authentication is about proving you have the right to access certain information. Authentication procedures generally fall into three categories: what you know, what you have, and who you are. An effective cybersecurity protocol will use a mix of techniques.
Passwords and security questions are classic “what you know” measures. But not all passwords are equally secure. All company passwords should be at least eight characters long and contain a mix of symbols to make them harder to guess.
A 12-character password with a mix of numbers, letters, and special characters takes approximately 62 trillion times longer to crack than a password with just six lower-case letters. You can use a password manager if you think it is too hard to remember all the tricky passwords.
These complex passwords add an extra layer of security for your business, without any extra cost.
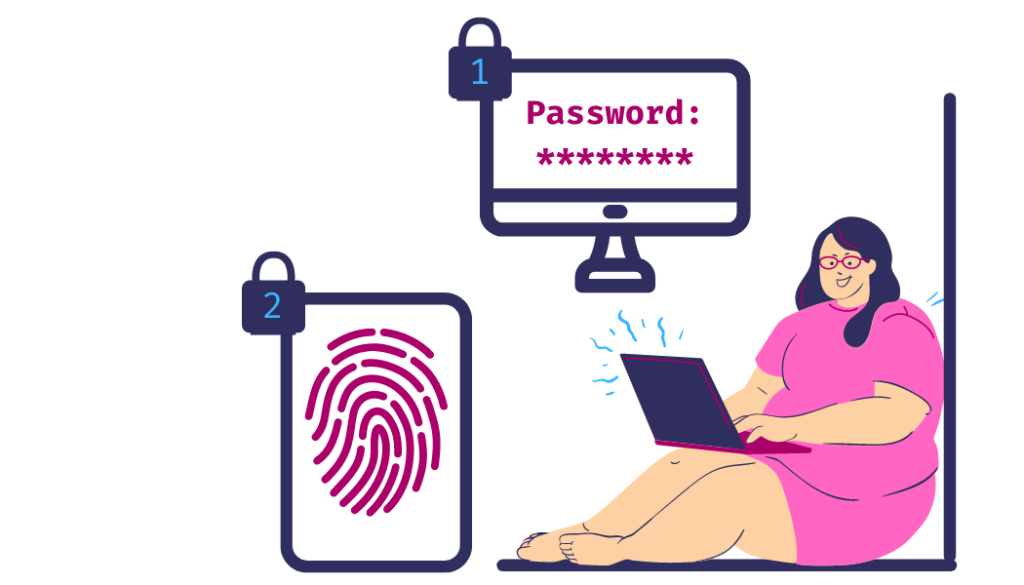
Multi-factor authentication
But what if a password isn’t secure enough? Multi-factor authentication relies on the user having access to two or more authentication methods.
For example, a user entering their password on a desktop will automatically receive a text to their phone with a secondary passcode. If a hacker does know that user’s password, it is extremely unlikely that they’ll also have their phone!
Other authentication strategies include facial recognition and fingerprint locks (if the device supports it), a verification email, and security questions.
Identify unusual activity
Passwords and security answers aren’t the only way to identify a user. Everyone has their own individual patterns and behaviors when they use technology, whether at work or at home.
Using AI and machine learning is a great way to spot common behaviors. Just like how social media algorithms learn what type of content we like, cybersecurity AI technology can recognize patterns in how a customer uses a service.
Then, if a user makes an out-of-character purchase or an unusual amount of requests, the AI will alert you of a possible cyber attack.

Train employees to be security-aware
People are the key to accessing sensitive information, so you need to train everyone in your company to be aware of cyber threats. This will make your business less vulnerable to socially engineered cyber attacks like phishing.
Regularly review these employee training programs and ensure they’re kept up to date. Foster a culture of learning when it comes to cybersecurity to keep everyone’s skills sharp.
Independent testing and validation
The security measures we’ve mentioned so far are things you can do internally. External service providers offer a high level of expertise and can assess how effective your cybersecurity measures really are.
The best outsourced software testing agencies and cyber risk assessors provide an outsider perspective on your company’s security. Like employee training, cybersecurity tests should happen regularly and inform future protocols.

Summary
The cybersecurity landscape is changing every day and every year new threats emerge and new tech to combat them is unveiled at the Cyber World Congress event. By using the simple security measures we’ve explained here, you can prevent cyber attacks and keep your business safe.
So, let’s review:
- System intrusion, social engineering, and denial of service attacks are some of the most common cyber threats
- Complex passwords with a mix of characters are much harder to crack
- Multi-factor authentication combines passwords with other security measures like biometrics
- Algorithms that notice patterns in users’ regular activity can alert you to cyber threats before they happen
- Employee training is key to preventing socially engineered attacks
We hope you’ve found this article on how to prevent cyber attacks useful. Good luck with your cybersecurity strategy and remember to share these tips with your network!