An Exploration of an Author’s Groundbreaking Contributions to AI Copyright
Last October, I received an email with a hell of an opening line: “I fired a…

Last October, I received an email with a hell of an opening line: “I fired a…

The other night I attended a press dinner hosted by an enterprise company called Box. Other…
Windows Taskbar vs. Apple Dock: A Comparative Analysis Windows Taskbar Pros: Efficient Application Management with…

Forget artificial intelligence breaking free of human control and taking over the world. A far more…

In November 2019, the US government’s National Security Commission on Artificial Intelligence (NSCAI), an influential body…
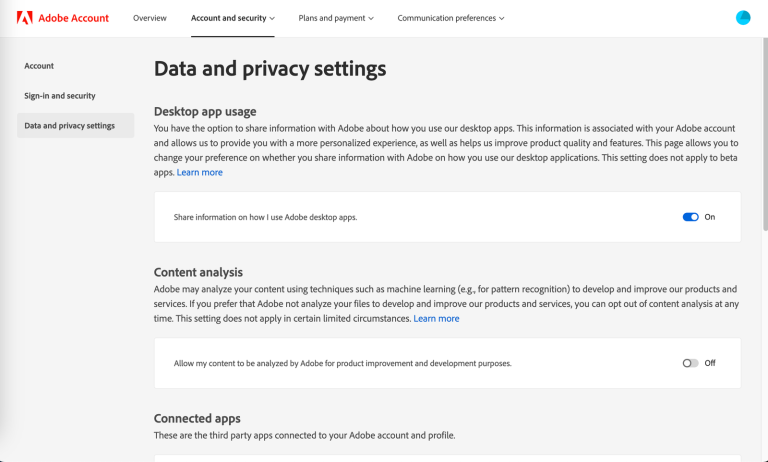
If you’ve ever posted something to the internet—a pithy tweet, a 2009 blog post, a scornful…

You answer a random call from a family member, and they breathlessly explain how there’s been…

Financial privacy has practically vanished over the last 50 years. Most people are in denial about…

We’ve all been astonished at how chatbots seem to understand the world. But what if they…

For the past few months, Morten Blichfeldt Andersen has spent many hours scouring OpenAI’s GPT Store….

Yes, San Francisco is a nexus of artificial intelligence innovation, but it’s also one of the…

Apple and Google are reportedly in cahoots to integrate features from Google’s Gemini generative AI service…

Whether you’re a student, a journalist, or a business professional, knowing how to do high-quality research…

Ever since the rollout of ChatGPT in November 2022, many people in science, business, and media…

This past Monday, about a dozen engineers and executives at data science and AI company Databricks…

I think the iPhone is a great piece of tech, but there are a couple of…

As AI-powered image generators have become more accessible, so have websites that digitally remove the clothes…

The current state of privacy is bad. Surveillance today is pervasive, and the effects of this…